Learn about resources for Risk & Compliance Teams

Data transfer regulations: Impact on Swiss and USA companies
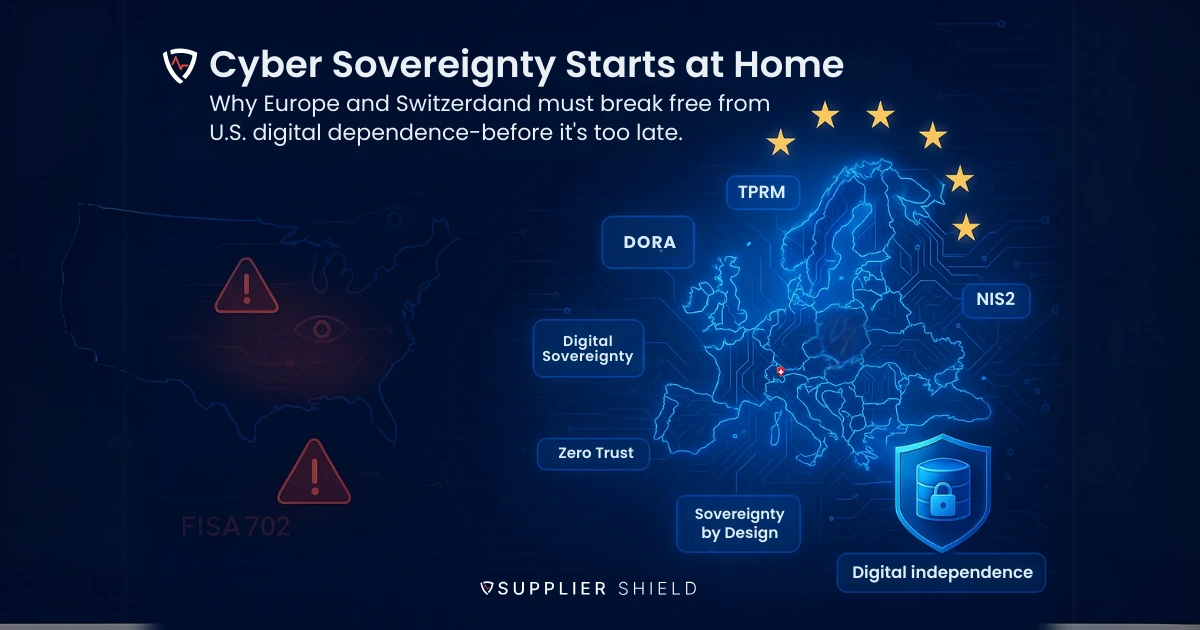
Discover how data transfer regulations impact Swiss and U.S. companies. Learn about the Swiss FADP, U.S. national security rules, and how Supplier Shield helps businesses navigate compliance with expert advisory, managed services, and a secure cloud platform.
.png)
.png)
.png)
.png)
.png)
.png)

.webp)

.png)
.webp)